Protect Your Mac From Hack Pop Up
Jun 02, 2015 How to protect your Mac from the ‘Dark Jedi’ firmware hack A new exploit dubbed ‘Dark Jedi’ exists for MacBook systems created before mid-2014, where a hacker can issue a malicious program to overtake the system’s firmware by simply having the system be put in sleep mode. Jan 17, 2020 Offering protection against both new and existing threats, Norton for Mac provides advanced, multi-layered security. It incorporates sophisticated anti-malware, anti-phishing, anti-ransomware, and anti-virus features, along with a smart firewall to safeguard your information and privacy against malicious attacks. Version Reviewed: 8.1.2; System Requirements: OS X 10.10.
A new exploit dubbed ‘Dark Jedi’ exists for MacBook systems created before mid-2014, where a hacker can issue a malicious program to overtake the system’s firmware by simply having the system be put in sleep mode. Upon waking from sleep, the firmware on these older Macs is unlocked, which leaves them open to access and modification from applications running in OS X. This contrasts with the recent Thunderstrike firmware vulnerability that allowed hackers to overtake firmware, but required physical access to the system. Since this current vulnerability is run by way of malicious software, systems can be attacked remotely by uses of trojan horse and other social engineering approaches, but this also provides an avenue for protection.
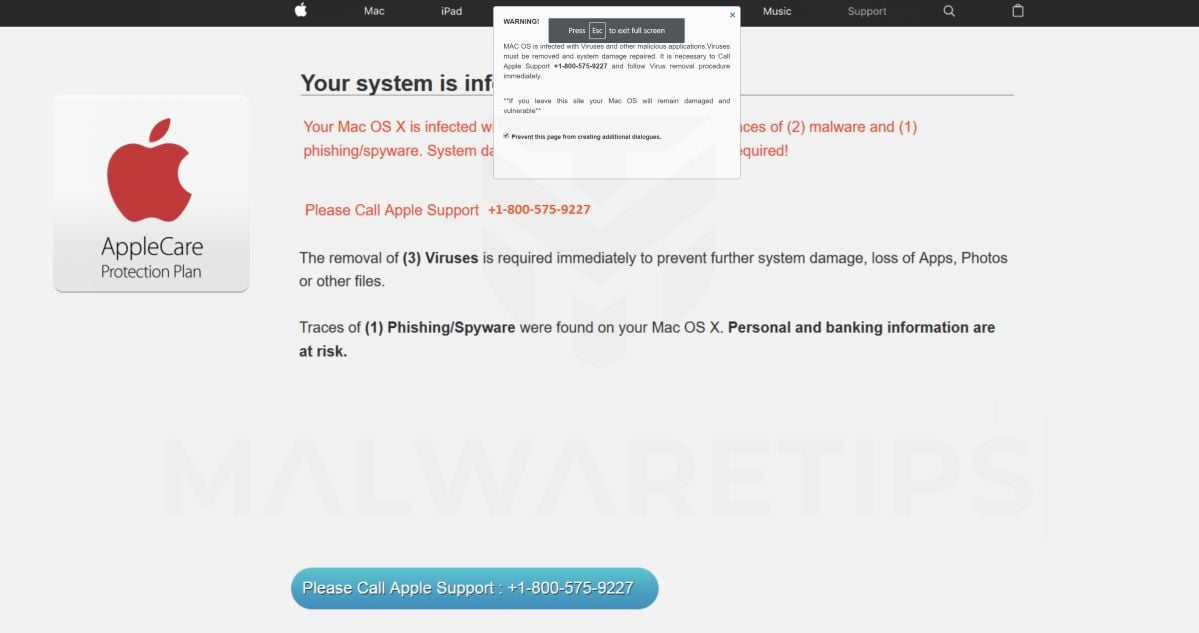
- I keep getting a pop up screen announces that my computer has been hacked with something and The 800 # I called told me for $200 they can fix the problem. It is coming up at least once a week now. My security settings are saying they are ok, but I have to turn off.
- Pop-up message that the computer has been locked because it may be infected In the middle of browsing the internet my screen flashed a message that my computer has been locked because it may have been infected. I recently installed Windows 10. There is a phone number to call. I did call the number but it is not identified as Microsoft.
If your Mac is an older one and you are concerned about this vulnerability, keep in mind that for now this is a proof-of-concept attack that is not known to be in any active hacking attempts. In addition it has three key limitations:
- It requires root access
- It requires you download it
- It requires your system be put to sleep
Only download software from developer sites or reputable software distributors
If you see a notice about a software update required for your system, then consider closing it and going to an official and known source for obtaining the latest version of that software package. For instance, if you are notified about an Adobe Flash or Java update, then go to the corresponding system preferences pane and use the update features in there, or go to Adobe’s Oracle’s, or any other relevant developer’s Web site to download standalone installers. For other software, use similar built-in software updaters and services like Apple’s Mac App Store for getting updates.
Judging potentially malicious sites can sometimes be difficult, but legitimate developers will usually channel you directly to appropriate and desired updater, whereas malicious sites often show many popups (some of which may download unwanted installers to your system), numerous ads, free deals and other offers, and redirect you to sites you did not intend. If any of these occur when browsing the Web, close them down and avoid interacting with them.
Be cautious about any package or installer you run on your Mac
Protect Mac From Malware
Whenever you are asked for your password, OS X system is attempting to escalate privileges to modify system resources. Therefore, if you see any notice on your Mac that asks you to enter your password, then be wary of it.
By only supplying your password when you need to specifically modify a setting, or are running a software installer that you trust and know the source of, then you will almost guarantee that you will avoid malware packages such as this one. If you even slightly suspect a package or installer, then delete it from your system and re-download it from the developer’s site.
Protect My Mac
Simcity buildit hack no survey mac. Don’t allow your Mac to go to sleep
Protect Your Mac From Hack Pop Up Windows 10
Even though this aspect of the Dark Jedi hack requires you have already installed the malicious software, this particular hack exploits the vulnerability where the firmware is left unlocked during sleep mode. This means that for now its mode of attack is when your Mac goes to sleep. While sleep mode is great for quick and convenient resuming of your workflow, OS X implements autosave and resume for resuming your workflow when your Mac boots. Therefore, in many cases you can similarly pick up where you left off by shutting your Mac down instead of sleeping it. To prevent system sleep, check the option to do so for each power profile in the Energy Saver system preferences pane.